Cloudlets Architecture and Main Functionality
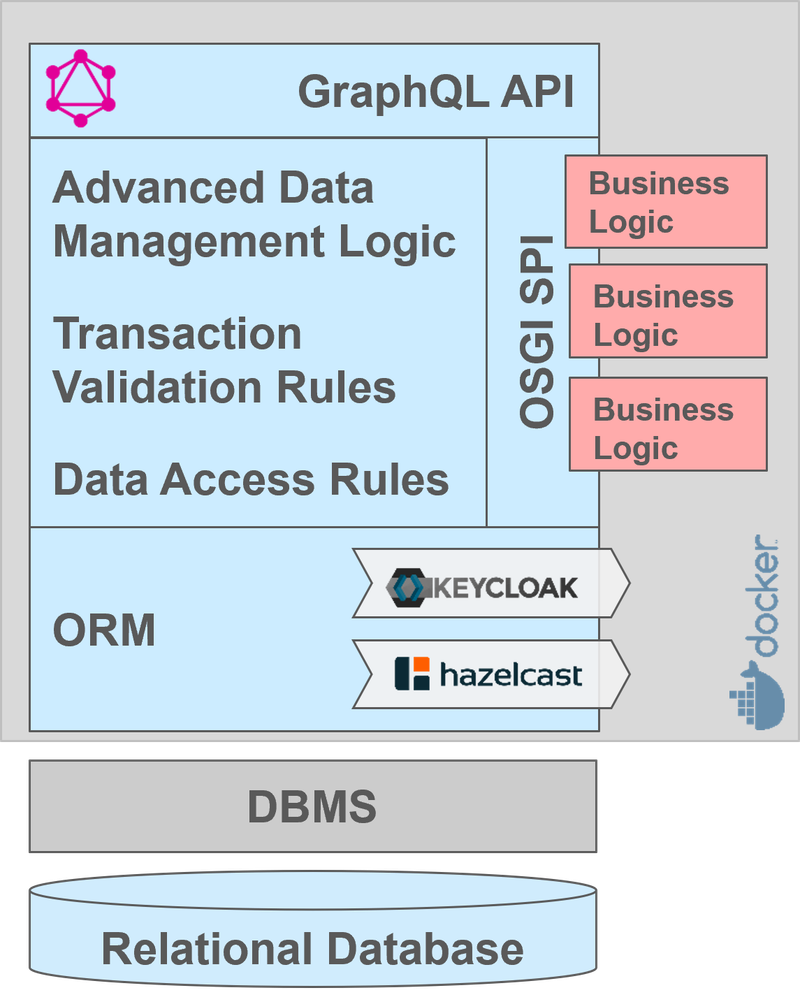
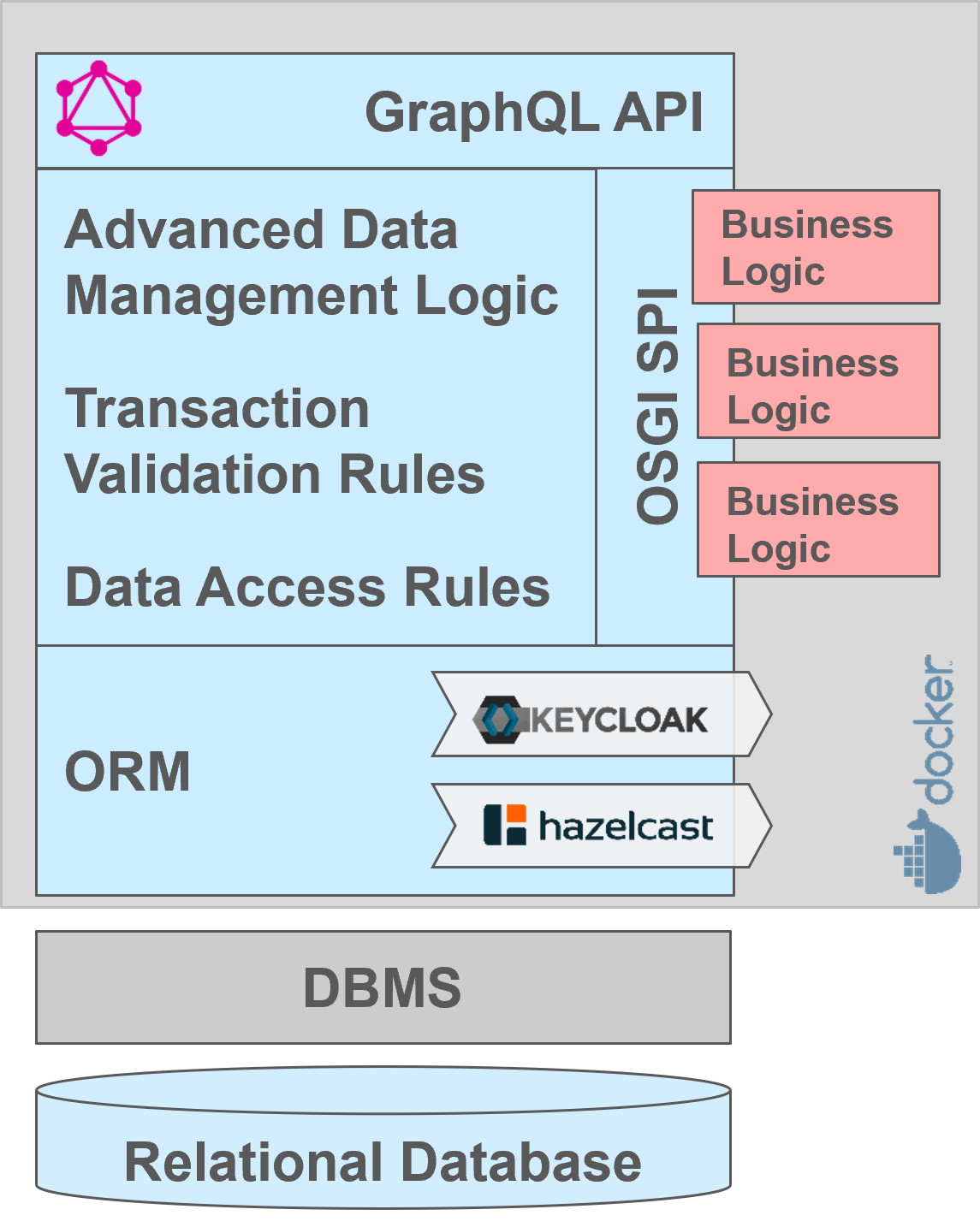
Cloudlets are headless server components generated by Livebase from high-level conceptual Models, without coding. They provide advanced (business-level) transactional data services via a secure GraphQL API.
Models can be interactively drawn, as layered diagrams, using the Livebase Designer. Each layer of a Model defines a specific aspect of the Cloudlet that will be generated of it: the conceptual structure of the data it will manage, the data-quality rules and transaction-validation rules it will enforce, the user profiles and the access-control rules defining the permissions of each user profiles.
Depending on the Model it's generated from, a Cloudlet can range in complexity and functional size from a simple microservice, to a Packaged Business Capability (as defined by Gartner), up to the entire backend of a business applications.
Each Cloudlet manages its own relational database via a rock-solid open-source DBMS (MariaDB) and a custom high-performance ORM. A layer of data-management logic (generated in Java) guarantees that any transaction performed on the database respects the data-quality rules, the transaction-validation rules and the access-control rules defined (without coding) in the Model. Such rules can be way more sophisticated and expressive than the ones supported by the underlying DBMS.
Multiple instances of a given Cloudlet can run concurrently, to support high-availability and horizontal scalability requirement. All the different instances of a Cloudlet can transparently operate on the same data by means of a concurrency-control algorithm running on a distributed in-memory database bases on the open-source Hazelcast technology. In this scenario, only the rule-enforcement logic and the GraphQL API will actually be replicated, and their instances will all access and manage the same database. Nevertheless, database horizontal scalability can be still achieved with specific MariaDB multi-node clustering (e.g. with Galera or SkySQL).
Every Cloudlet comes with a built-in users registry and authentication system, but it can be configured (without coding) to rely on an external instance of Keycloak (a widely used open-source identity and access management) to support Single-Sign-On configurations.